Vulnerability reachability analysis¶
What is reachability
Reachability analysis checks whether a potentially vulnerable piece of code can actually be executed when using the application. This allows filtering out the "noise" and focusing on exploitable issues.
Johnny CLI agent can analyze whether vulnerabilities are reachable from source code.
To use this feature, you need to set two parameters:
cg-path— path to the Svace-format call graph;cg-lang— programming language for which the call graph was built. Currently, onlyjavais supported.
Building the call graph¶
Using Svace¶
- Download the Svace module
https://REGISTRY_USERNAME:REGISTRY_PASSWORD@REGISTRY_URL/#browse/browse:files:codescoring%2Fsvace-callgraph - Obtain a user token in CodeScoring (
/cabinet/profile) - Run Svace on the project's source code. This step is best performed within or after the build stage in your CI/CD pipeline.
- Initialization
- Instrumented build
- Analyze results and generate the call graph
- Upon successful completion of all steps, a file named
.svace-dir/analyze-res/call-graph/<project_name>-graph-order.jsoncontaining the call graph will appear in the project directory. - Launch the scan using Johnny, for example:
Viewing results¶
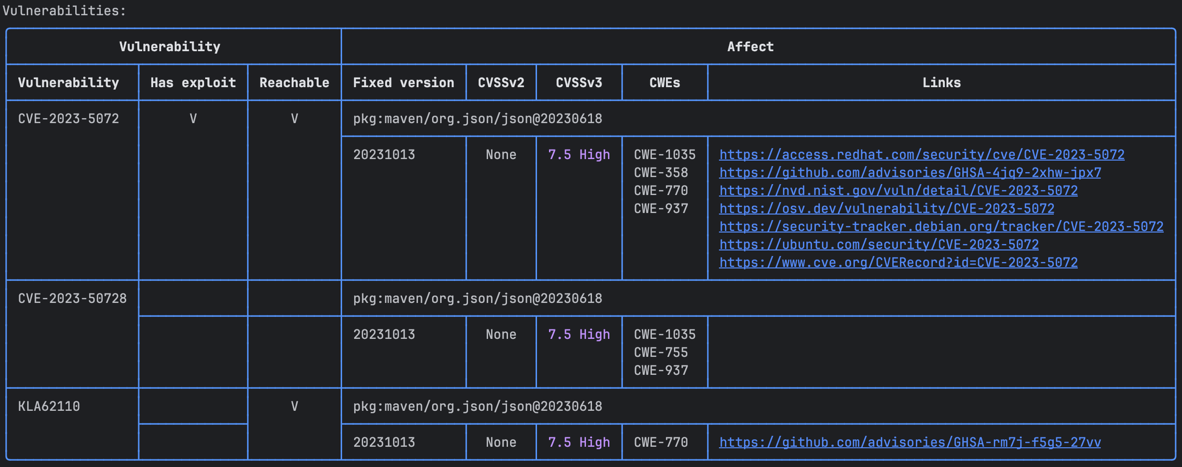
In the vulnerabilities table, vulnerabilities with identified reachable call paths will be marked in the corresponding column:
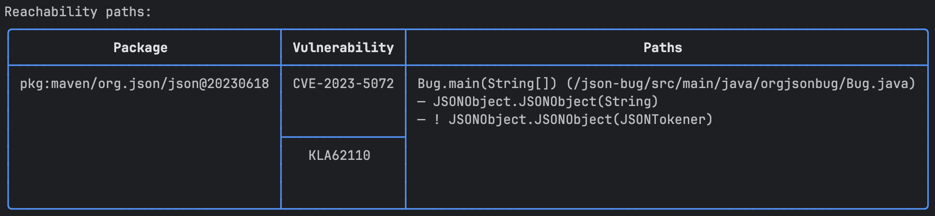
Additionally, at the end of the report, another table listing the call trees for vulnerabilities will be available:
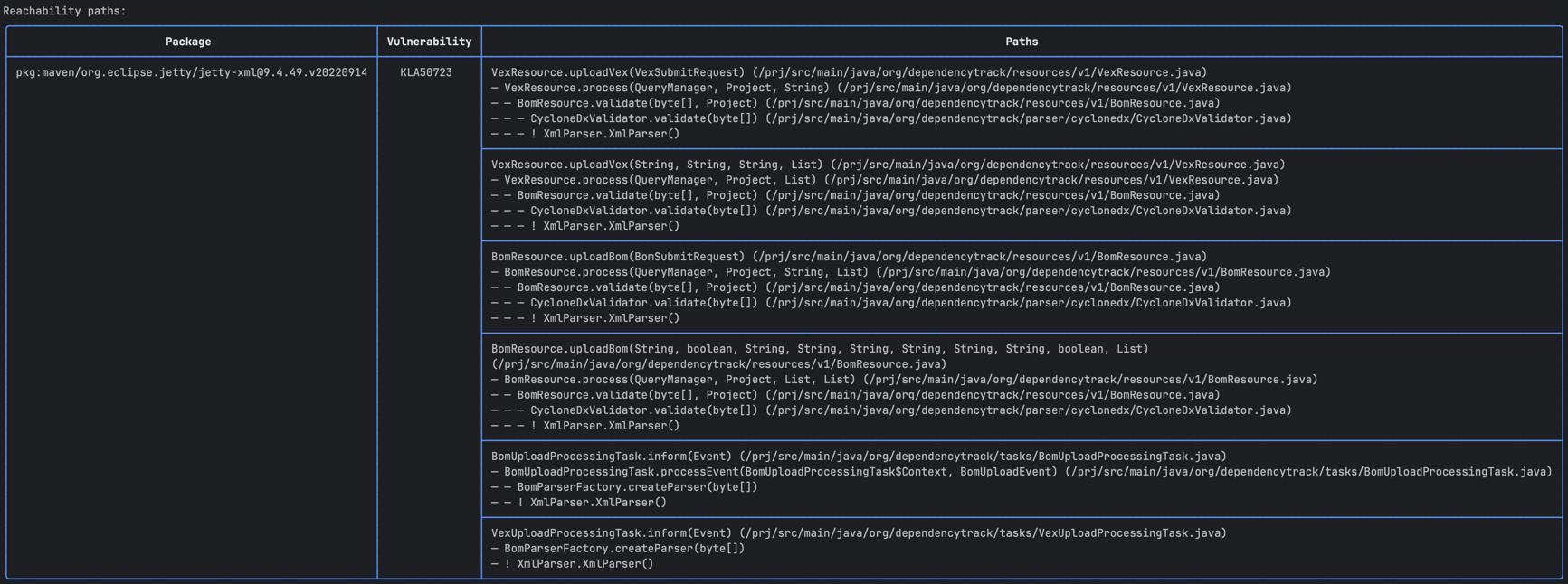
Example for a larger project:
If the --save-results flag was specified, reachability results will appear in the "Reachable" column of the vulnerabilities table: